- Do not include sensitive data such as passwords, confidential project details, Controlled Unclassified Information (CUI), Federal Contract Information (FCI), Covered Defense Information (CDI), or any information classified as confidential or restricted.
Procore for Government
Table of Contents
- Overview
- Key Features
- Product Deep Dive
- Product Modules
- Getting Started Guides
- Tutorials
- Commercial Documentation
- Release Notes
- Shared Responsibility Model
- Contact Support
Overview
PROCORE FOR GOVERNMENT
Available Procore for Government Tools are engineered consistent with the FedRAMP Moderate baseline.
|
|
Welcome to the Procore for Government support site page. The government platform is designed to provide a secure and robust solution intended solely for use on public sector construction projects, not commercial construction.
|
What this means for you
-
Top-Tier Security: Designed for organizations requiring federal-grade security, Procore for Government helps federal agencies and DoD contractors simplify compliance with rigorous standards like Cybersecurity Maturity Model Certification (CMMC) Level 2.
-
Trusted Partnership: Procore for Government has achieved FedRAMP® Moderate Authorization and is listed as "Authorized" on the FedRAMP Marketplace
.
-
Streamlined Agency Compliance and Audit-Readiness: Procore for Government helps agencies achieve compliance by capturing structured data on a secure platform that helps drive user adoption.
-
A Unified Platform: Procore for Government unites every project team on a single, secure platform. Public agencies, program managers, and owners can manage all phases of construction in one place.
-
Total Project Visibility: Organizations gain a single source of truth across all projects and programs, with real-time dashboards and reporting for proactive oversight.
-
Accelerated Collaboration: Unified collaboration tools in a FedRAMP Moderate Authorized environment and Customer Data within the Procore for Government platform hosted and processed in the United States.
-
Secure Field Mobility: Procore for Mobile (iOS/Android) securely connects to the Procore for Government platform, protecting data in transit with Federal Information Processing Standards (FIPS)-validated encryption. Mobile functions mirror the authorized tools to maintain security and compliance controls in the field
Key Features
PROCORE FOR GOVERNMENT
Available Procore for Government Tools are engineered consistent with the FedRAMP Moderate baseline.
Procore for Government is FedRAMP® Moderate Authorized and is listed as “Authorized” on the FedRAMP Marketplace . The platform helps U.S. public agencies and their contractors manage complex construction projects.
Procore for Government delivers the proven power of our industry-leading platform in an environment designed to conform with public sector security standards:
- The Procore Platform: Procore for Government delivers a flexible, scalable platform for organizations. Tailor the solution by combining core modules—like Project Execution, Financial Management, and Construction Intelligence.
- Government-Grade Security: Hosted on AWS GovCloud (US), Procore for Government is FedRAMP® Moderate Authorized, featuring mandatory Multi-Factor Authentication (MFA), strong password policies, and secure account management.
- Dedicated Government Environment: The unique 'Procore for Government' logo and login screen set the platform apart from the commercial version of Procore. Before logging in, users must also acknowledge they are accessing a government system and consent to standard monitoring and auditing.
To learn more about Procore for Government, visit:
- For government agencies: https://www.procore.com/government
- For public sector: https://www.procore.com/public-agencies
Experience Overview
PROCORE FOR GOVERNMENT
Available Procore for Government Tools are engineered consistent with the FedRAMP Moderate baseline.
The Procore for Government platform is designed to provide a secure and robust solution intended solely for use on public sector construction projects, not commercial construction. While the core tools and user experience are closely aligned with Procore’s commercial platform, the key difference is its separate, secure foundation—all project data is managed in an environment designed for government data use.
This guide explains the main features of Procore for Government.
The Procore for Government Experience
This table highlights the government platform's features and security.
| Category | Description |
|---|---|
| Procore for Government Zone | Procore for Government runs on the AWS U.S. Gov Zone, a separate platform from our commercial version. Because the platforms are separate, end users cannot transfer project data between the commercial and Procore for Government environments. The U.S. Gov Zone is designed for higher security, which means some features found in the commercial version of Procore are limited, operate differently, or are unavailable. |
| Application Experience | The Procore for Government application has a distinct 'Procore for Government' logo, login requirements, and legal notices. The user interface may also appear different from the commercial platform, as features and enhancements in the commercial platform can only be updated in the Procore for Government platform after meeting FedRAMP standards. |
| Mobile Experience | The commercial Procore mobile app can be connected to the secure U.S. Gov Zone. Access to the Zone is strictly controlled with Multi-Factor Authentication (MFA). Data is secured with FIPS-validated encryption. Mobile apps can only be installed on authorized, government-issued, and managed devices. End users are required to report any lost, stolen, or compromised devices to their incident response team immediately. |
| Platform Updates | Procore for Government updates are released quarterly. |
| Partner Ecosystem and Integrations | Procore for Government offers a dedicated, separate partner ecosystem. All third-party applications are integrated through this ecosystem consistent with the FedRAMP® Moderate baseline. Direct API integrations are not permitted. Data transfer must be performed using secure CSV files. Integrations approved for Government use are available at the Procore for Government App Marketplace |
Application Experience
PROCORE FOR GOVERNMENT
Available Procore for Government Tools are engineered consistent with the FedRAMP Moderate baseline.
Procore for Government is a secure, cloud-based construction management platform specifically designed for public sector projects. It provides a single, controlled environment where government agencies and their authorized contractors can collaborate on their projects.
The platform is accessible via a secure web browser or the Procore mobile app, enabling work from the office or the field.
The Application Experience
Procore for Government acts as the unified hub for all project information, allowing stakeholders to work from the same set of documents and data. The user interface provides a clear, at-a-glance view of project health, pending tasks, and recent activity.
To visually distinguish this secure environment from the commercial version of Procore, the platform features a unique Procore for Government logo, specific login requirements, and in-app legal notices.
Key Solutions
Procore for Government includes a suite of integrated tools to manage these aspects of public sector construction projects:
- Preconstruction. Consolidates designs, bids, and estimates into a single solution. This centralized approach allows for planning through early stakeholder validation and clash detection, while also allowing you to refine your future project backlog based on historical performance.
- Project Execution. Centralize your public sector project information for all stakeholders. This single source of truth helps identify schedule and budget impacts.
- Financial Management. Centralize financial data for real-time visibility into project and portfolio health. This unified view enables forward-looking forecasts, change management, and reporting.
- Construction Intelligence. Consolidates data into a common system for analysis. This aligns stakeholders on a single source of truth to gauge financial and performance health.
To help ensure stability and security, updates to Procore for Government are released quarterly after being developed and tested in the commercial environment.
Security Built for the Public Sector
Security is foundational to the Procore for Government platform. Procore for Government is FedRAMP Moderate Authorized, which helps support contractors who may have CMMC (Cybersecurity Maturity Model Certification) Level 2 obligations.
- Secure Environment: All Procore for Government accounts are created in the secure, separate U.S. Gov Zone to ensure data is completely isolated from the commercial platform. Only certified Procore personnel manage this data and resolve any issues.
- Controlled Authentication: All end users are required to securely log in using approved methods, including Single Sign-On (SSO), Multi-Factor Authentication (MFA), and Personal Identity Verification (PIV) and Common Access Cards (CAC).
- Managed Platform Stability: To maintain a secure and stable environment, platform updates are developed and tested on the commercial platform before being released on a predictable quarterly schedule for government clients.
Mobile Experience
PROCORE FOR GOVERNMENT
Available Procore for Government Tools are engineered consistent with the FedRAMP Moderate baseline.
The Procore Mobile app provides teams with secure access to the Procore for Government platform directly from their iOS and Android devices. It’s an essential tool for keeping field and office personnel connected.
The Mobile Experience
Access is strictly controlled to protect sensitive project information. To log in, users require Procore for Government credentials and must use Multi-Factor Authentication (MFA) to verify their identity. This helps to ensure that the security permissions set up in the Procore for Government platform are enforced on mobile devices. All data transmitted to and from the Mobile app is protected using Federal Information Processing Standards (FIPS)-validated encryption. The Mobile app also works offline, automatically syncing all data once a connection is re-established.
Download the Procore Mobile App
The commercial Procore Mobile app (iOS/Android) can be downloaded from these links and must be installed on a government or contractor-issued device. Users will see login links for both the commercial and Procore for Government environments. Only users with existing access to the Procore for Government environment can log in and are required to use Multi-Factor Authentication (MFA) to log in to Procore for Government below:
Rules of Behavior for Mobile Users
All personnel accessing the Procore for Government environment via a mobile device must adhere to the following security protocols.
- Device Authorization
- Government-Managed Devices Only: Procore Mobile apps must be installed and used exclusively on devices issued and managed by your organization or an authorized contractor.
- Prohibition of Personal Devices: The use of personal or any other unmanaged devices to access the Procore for Government environment is strictly prohibited.
- Device Security and Data Management
- Secure Login: Mobile users are required to use Multi-Factor Authentication (MFA) to gain access to Procore for Government from the Mobile app.
- System Updates: Please refer to your organization’s Customer Responsibility Matrix for more details on mobile device management.
- Device Encryption: On-device storage must be encrypted at all times using FIPS-validated encryption modules.
- Incident Reporting
- Immediate Notification: Any actual or suspected loss, theft, or compromise of a device used to access Procore for Government must be reported immediately to the designated agency or organization’s incident response team.
Partner Ecosystem
PROCORE FOR GOVERNMENT
Available Procore for Government Tools are engineered consistent with the FedRAMP Moderate baseline.
The Procore for Government Partner Ecosystem operates on a distinct, secure platform tailored for Procore for Government. It operates within a controlled environment, utilizes a separate API, and offers a Procore for Government-only app marketplace.
Partner Ecosystem Experience
The Procore for Government platform extends its functionality through a dedicated Partner Ecosystem. This secure, isolated environment features a Procore for Government only App Marketplace, a separate API for developers, and robust administrative controls.
Procore for Government App Marketplace
Integrations for Procore for Government are available on a dedicated Procore for Government App Marketplace. Only pre-approved applications meeting certain security standards, including validated encryption and role-based access controls for all data transfers are included. For more information, reach out to your Procore for Government Point of Contact. The Procore for Government App Marketplace has a unique logo and URL (marketplace.procoregov.com ) to distinguish it from the commercial site. Access is restricted to authorized Procore for Government users.

App Management
Procore for Government's App Management tool allows administrators to install pre-approved applications from Procore and third-party partners. Installation is available through two methods: selecting from the dedicated Procore for Government App Marketplace or installing a pre-approved custom integration using a specific App Version ID.
Current integrations include:
- Third-Party Applications: Visit marketplace.procoregov.com
for the list of available apps.
- Procore-Built Applications: Procore Drive (Windows) and Procore Imports (Windows). When connecting Procore Drive to Procore for Government, users must select the checkbox to connect to the government instance on the Settings page.
To help protect project data, information can only be transferred to external accounting or ERP systems using secure Comma-Separated Values (CSV) files. The App Management tool can be found in the Procore for Government Company Admin tool.

Procore for Government: Developers
The Procore for Government environment uses a separate API. Documentation is available on a dedicated Procore for Government Developers site. This offering is designed exclusively for U.S. government customers who require higher levels of security, compliance, and data governance. For more information, please refer to the Procore Federal Environment Overview .
The Procore for Government developers site has a unique logo and URL (developers.procoregov.com ) to distinguish it from the commercial site.

Platform Features
PROCORE FOR GOVERNMENT
Available Procore for Government Tools are engineered consistent with the FedRAMP Moderate baseline.
Procore for Government's suite of integrated tools allow for secure document management and real-time field data collection to formalized financial workflows and unalterable audit trails providing government agencies and their contractors with a complete picture of project performance.
Document and Drawing Management
- PDF Viewing & Markup: View PDF documents and drawings directly within the platform. Markup tools allow users to add text, callouts, shapes, highlights, and free-form drawings to documents and plans for sharing with stakeholders.
- Version Control: Manage version control on uploaded documents and drawings, giving everyone on the team visibility to the latest set. Older versions are archived and remain accessible for reference.
- Collaborative Annotations: Authorized users can add comments and annotations to documents, creating a clear record of feedback and changes.
- Drawing Hyperlinking: Scan drawings and create hyperlinks between different sheets and details, making navigation quick and intuitive.
- Document Search: Search features allow users to find matching information within documents and drawings, not just by filename.
Field and Site Management
- Mobile Plan Viewing: Permissions-based access to project drawings and documents directly from a government-managed computer or mobile device.
- Daily Log Creation: Create daily logs documenting weather and site safety observations. Photos can be attached directly from a government-managed computer or mobile device.
- Photo & Video Management: Upload photos and videos and manually tag them for the official project record by location and trade, and share with project stakeholders.
- Punch List & Inspections: Create and manage punch lists and inspection items directly from the field. Assign items to the responsible contractor, set due dates, and track their resolution with photo verification.
Project Communication and Workflow
- RFI (Request for Information) Management: Allows users to create, submit, and track RFIs. Procore for Government routes items to the appropriate reviewers and maintains a change history with date/time stamps.
- Submittal Packages: Create, send, and track submittal packages electronically. Reviewers can use markup tools to approve, reject, or comment on submittals.
- Financial Management: Create and manage custom approval workflows for Budget, Commitments, Document Management, Directory, Invoicing, and Prime Contracts.
- Change Management: Offers dedicated change management tools to help teams formally navigate the change process, from creation to approval and financial impact tracking.
Reporting and Analytics
- Customizable Dashboards: Create custom dashboards to get a real-time overview of project health, including the status of RFIs, submittals, and budget items.
- Standard and Custom Reports: Generate a wide variety of standard reports or build custom reports to analyze project data. Reports can be scheduled to run automatically and be distributed to the project team.
- Audit Trail: Maintain a detailed and unalterable audit trail of project actions, including who viewed a document, when an RFI was answered, and when a submittal was approved.
Search Capabilities
Securely search for items by keyword within a specific project or tool.
Core Tools
PROCORE FOR GOVERNMENT
Available Procore for Government Tools are engineered consistent with the FedRAMP Moderate baseline.
Delivered within a secure and isolated cloud environment, Procore for Government's Core Tools provide a foundational hub for the organization and its construction projects. This creates a single source of truth to connect office and field teams, giving stakeholders real-time access to the most current project information.
Core Tools: Company
Procore for Government's company-level navigation menu provides authorized users with access to these core tools:
- Portfolio: Provides a high-level overview of all projects to monitor portfolio health with capabilities to view, search, group, and filter projects and dashboards.
- Directory: A centralized database for managing user contacts, companies, distribution groups, and permissions.
- 360 Reporting: Access project data to build custom reports and visual dashboards, with data export to CSV or PDF.
- Documents: A centralized repository to store and organize files while controlling access and tracking version history.
- Workflows: Create and manage approval workflows for Budget, Commitments, Documents, Directory, Invoicing, and Prime Contracts.
- Admin: Provides functionality for managing company settings, project settings, and tool settings.
- App Management: Provides a centralized place for administrators to install, configure, and manage applications from the Procore for Government App Marketplace. Installation of custom apps requires an App Version ID. For more information, reach out to your Procore for Government Point of Contact.
- Permissions: Manage user permissions and create company and project permission templates for granular control.
- Procore Analytics: Transforms your company's project data into interactive dashboards and reports using Procore Analytics 2.0.
Core Tools: Project
After navigating to a project, Procore for Government's project-level navigation menu provides authorized users with access to these core tools:

- Home: A central dashboard providing an at-a-glance summary of important updates and project health, featuring the unique branding of Procore for Government. It only displays information from tools available in the Procore for Government environment.
- 360 Reporting: Access project data to build custom reports, visual dashboards, and export data to CSV or PDF.
- Documents: A centralized project repository for documents with in-app upload functionality.
- Directory: A centralized database for managing user contacts, companies, distribution groups, and permissions on a project.
- Tasks: Create a traceable record of all assigned tasks with functionality to create, assign, track, and view them.
- Admin: Manage configuration and permission settings for an individual project.
Analytics
PROCORE FOR GOVERNMENT
Available Procore for Government Tools are engineered consistent with the FedRAMP Moderate baseline.
Procore Analytics 2.0 is a Business Intelligence (BI) tool within the Procore for Government platform. It enables public sector clients to monitor project performance, identify risks, and support data-driven decision-making within a secure, isolated environment.
Procore Analytics 2.0
Authorized users can access Procore for Government's Analytics tool, Procore Analytics 2.0, from the company navigation menu. Click Procore Analytics.
Key Features
Key Tool: Procore Analytics 2.0
Key features include:
- Comprehensive, Updated Data: Users can generate reports from a wide range of Procore for Government project data, which is refreshed hourly.
- Secure Export of Procore for Government Data for Offline Analysis: To maintain a secure environment, Procore for Government does not permit direct, live integrations with third-party applications or embedded dashboards. The required workflow is to manually export reports as CSV or PDF files for offline analysis.
- Strict Account Segregation: Data from a Procore for Government account cannot be combined or accessed with other Procore for Government accounts under a single API token, creating a strict separation between secure government projects and other data.
Important
Once data is exported from the Procore for Government platform, users are responsible for handling, storing, and sharing the data in a manner that complies with all of your organization's security and data handling policies.Bid Management
PROCORE FOR GOVERNMENT
Available Procore for Government Tools are engineered consistent with the FedRAMP Moderate baseline.
Procore for Government's Bid Management solution offers a centralized platform designed to simplify and streamline the entire bidding process, from creating bid packages to awarding contracts. This powerful tool provides a single source of truth for all bidding-related activities.
Bid Management Tools
Authorized users can access Procore for Government's company-level Bid Management tool, Planroom, from the company navigation menu. Click Planroom.

Authorized users can also gain access to Procore for Government's project-level Bid Management tool, Bidding, from the project navigation menu. Click Bidding.
Key Features
Key Tools: Bidding, Planroom
- Centralized Bid Packages: Create comprehensive bid packages with all necessary plans, specifications, and documents in one location, ensuring all bidders have identical information.
- Efficient Bidder Management: Invite and manage bidders from a company directory, track their status (e.g., "Intends to Bid," "Bid Submitted"), and automatically log all communications.
- Standardized Bid Submissions: Utilize standardized bid forms to receive bids in a consistent format, simplifying the comparison process.
- Side-by-Side Bid Leveling: Analyze submitted bids in a comparative view to identify discrepancies and determine the best value for the project.
- Seamless Contract Conversion: Convert an awarded bid directly into a subcontract or purchase order within a Procore for Government project's Commitments tool, streamlining the transition to project execution.
Important
Prequalification requirements vary significantly across different government agencies. Therefore, Procore for Government users must follow their organization’s official process to prequalify bidders before inviting them to bid in Procore for Government.BIM
PROCORE FOR GOVERNMENT
Available Procore for Government Tools are engineered consistent with the FedRAMP Moderate baseline.
Procore for Government's Building Information Management (BIM) solution empowers public sector teams by making complex 3D models accessible and actionable on a single, secure platform. This suite of integrated tools enables all authorized stakeholders to interact with data-rich models and tie them directly to critical project management workflows, from office coordination to issue resolution in the field.
BIM Tools
Authorized users can access Procore for Government's BIM tools from the project level navigation menu. Under Core Tools, click Documents. Under Project Management, click Drawings, Coordination Issues, and Models.

Key Features
Key Tools: Documents, Drawings, Coordination Issues, Models
Key features include:
- Centralized Model Access: View and interact with 3D models directly on Procore for Government's web and mobile applications, making BIM accessible to all authorized team members.
- Intuitive Navigation: Easily navigate complex, consolidated models with simple controls to orbit, pan, and zoom, and use sectioning tools to see inside the model.
- Embedded Data on Demand: Instantly view rich metadata, such as material specifications and dimensions, by simply clicking or tapping on any object within the 3D model.
- Model-Based Issue Creation: Create and pin Coordination Issues directly onto components in the model to clearly identify, assign, and track clashes or constructability problems.
- Integrated Project Management: Generate RFIs and Observations directly from the 3D model, automatically linking them to the relevant objects to provide clear context for field and office teams.
- Discipline Filtering: Isolate specific building systems within the model (e.g., mechanical, electrical, structural) for simplified and focused reviews.
Important
Procore for Government does not support Procore BIM Plugins or integrations with third-party design applications. All 3D model interaction occurs exclusively within the secure Procore for Government platform.Invoice Management
PROCORE FOR GOVERNMENT
Available Procore for Government Tools are engineered consistent with the FedRAMP Moderate baseline.
Procore for Government's Invoice Management provides a controlled and auditable invoicing process allowing payments to be reviewed, documented, and aligned with each project's contracts, providing a complete, defensible financial record for every construction project.
Invoice Management Tools
Authorized users can access Procore for Government's BIM tools from the project level navigation menu. Under Financial Management, click Prime Contracts (or Funding for owners), Commitments, and Invoicing.

Key Features
Key Tools: Prime Contracts / Funding, Commitments, Invoicing
Key features include:
- Centralized Invoice Tracking: Gain complete visibility into the status of all subcontractor and owner invoices for any given billing period from a single dashboard.
- Streamlined Invoice Creation: Simplify the creation of both owner and subcontractor invoices. You can invite subcontractors to bill directly in the system or create invoices on their behalf.
- Automated Billing Periods: Set up automatic billing periods that align with your accounting cycles to standardize the invoicing schedule across projects.
- Collaborative Review and Approval: Customize invoice approval workflows to route invoices to the appropriate stakeholders for review. Reviewers can approve or reject individual line items, preventing delaying entire payments.
- Prevention of Overbilling: Align invoice amounts with the actual work completed by linking them to the project's schedule of values and contract amounts.
- Customizable Invoice Generation: Use a configurable PDF builder to control the level of detail displayed on owner invoices, tailoring the format to meet specific client or project requirements.
- Attachment and Document Consolidation: Attach necessary backup documentation to invoices, ensuring all required information is submitted and stored in one organized place.
Important
All financial activities, including the exchange and tracking of lien waivers and the processing of all payments, must be conducted using your organization's own approved financial and payment systems. Procore for Government manages the documentation and approval workflows that precede a transaction; the final processing of funds must occur outside of the platform.Preconstruction
PROCORE FOR GOVERNMENT
Available Procore for Government Tools are engineered consistent with the FedRAMP Moderate baseline.
Procore for Government's Preconstruction tools consolidate key project data in a single solution. Managing documents, designs, bids, and budgets in one place enables faster "clash-free" design validation. Teams can also leverage historical performance data to optimize their project backlog.
Preconstruction Tools
Authorized users can access Procore for Government's Preconstruction tools from the project navigation menu. Click the Bidding tool under Preconstruction or click Coordination Issues, Drawings, and Models under the Project Management menu.

Key Solutions
Key solutions include:
Bid Management
Key Tools: Bidding, Planroom
Procore for Government's Bid Management solution digitizes and streamlines the entire bidding process, from creating bid packages to awarding contracts.
- Centralized Bid Creation: Create comprehensive bid packages, attaching relevant drawings, specifications, and models directly from the project's document repository.
- Streamlined Communication: Manage all bidder communication, including RFIs and addenda, within the platform to ensure all bidders have the same, up-to-date information.
- Bid Leveling: Compare bids submitted in a standardized format, allowing for true "apples-to-apples" comparisons to identify the best value.
Design Coordination (BIM)
Key Tools: Coordination Issues, Drawings, Models
Procore for Government's Design Coordination solution brings the Virtual Design and Construction/Building Information Modeling (VDC/BIM) process into the platform, allowing teams to find and resolve clashes.
- Model Aggregation: Upload and combine multiple 3D models from various design disciplines (e.g., architectural, structural, and more) into a single federated, viewable model in the cloud.
- Automated Clash Detection: Run clash detection tests to identify and group areas where different building systems interfere with one another.
- Coordination Issues: Create, assign, and track "Coordination Issues" directly from the 3D model, providing a clear and traceable workflow for resolving design conflicts among stakeholders.
Important
Procore for Government does not support direct publishing or uploads from third-party design applications (such as Autodesk Revit®, AutoCAD®, or Navisworks®). End users are solely responsible for ensuring the manual transfer of all design files—including drawings, models, and documents—is performed in accordance with their organization's security and data handling protocols. End users must export the necessary files from third-party design applications and manually upload them into the appropriate tool within the secure Procore for Government environment.
Project Execution
PROCORE FOR GOVERNMENT
Available Procore for Government Tools are engineered consistent with the FedRAMP Moderate baseline.
Collaborate and gain real-time visibility across your entire project with Procore for Government's Project Execution tools. This integrated suite centralizes all critical data—from daily logs and RFIs to safety inspections and punch lists—to create a single source of truth for each project.
Project Execution Tools
Authorized users can access Procore for Government's Project Execution tools from the project navigation menu. Click the tools under Core Tools or Project Management in the menu.
Key Solutions
Key solutions include:
Project Closeout
Key Tools: Documents, Drawings, Meetings, Punch List, RFIs, and Submittals
Deliver a comprehensive and professional digital turnover package that reflects the quality of your work. Because all project information is captured in Procore for Government throughout the construction lifecycle, closeout becomes a straightforward process of exporting a complete, organized record from essential tools.
Field & Task Management
Key Tools: Daily Log, Inspections, Observations, Photos, Tasks
Procore for Government's Tasks tool centralizes all project action items, allowing teams to create, assign, and track work in one place (instead of using scattered emails or spreadsheets). This assigns clear owners and due dates for every task, from simple reminders to critical path activities. The tool also streamlines communication and provides visibility into progress.
Assignment functions are also available. Users can document job site activity in the Daily Log and Photos tools and assign action items in the Tasks, Inspections, and Observations tools.
Project Management
Key Tools: Daily Log, Documents, Drawings, Inspections, Meetings, Observations, Photos, Punch List, RFIs, Specifications, Submittals
Centralizes project data to connect office and field teams with tools. Provides real-time access to the latest drawings, submittals, and field reports to every stakeholder.
Quality & Safety
Key Tools: Action Plans, Forms, Incidents, Inspections, Observations, Punch List
Centralizes data and workflows for teams. This allows teams to use mobile devices to document inspections, log observations, and report incidents in real-time. Every issue is then tracked from identification through resolution with clear accountability, creating a complete quality and safety record.
Project Financials
PROCORE FOR GOVERNMENT
Available Procore for Government Tools are engineered consistent with the FedRAMP Moderate baseline.
Eliminate disconnected spreadsheets and information silos by unifying all project financial data onto a single, collaborative platform. Procore for Government's Financial Management tools connect the budget, prime contract (or funding), commitments, and change orders, allowing every stakeholder to work with the same information.
Project Financials Tools
Authorized users can access Procore for Government's Financial Management tools from the project navigation menu.

Key Solutions
Key solutions include:
Budget Management
Key Tool: Budget
The core of the solution is the Budget, which serves as the single source of truth for the project's financial plan. Users can create a detailed budget with specific line items, lock it to prevent unauthorized changes, and track all costs against it. The system automatically updates budget data as costs are incurred and changes are approved, providing a current view of project financial health.
Prime Contract / Funding Management
Key Tools: Prime Contracts / Funding
The Prime Contracts tool (also called the Funding tool, for owners) manages the master agreement with the project owner, serving as the single source of truth for all project revenue. It's built around a detailed Schedule of Values (SOV), which breaks down the total contract into billable line items and is used as the basis for generating owner invoices.
Cost & Commitment Tracking
Key Tools: Commitments, Direct Costs
The Commitments and Direct Costs tools provide a centralized place to manage all expenditures, from formal commitments (e.g., subcontracts and purchase orders) to miscellaneous direct costs (e.g., field purchases), allowing users to log every expense against its corresponding budget code.
Change Management
Key Tools: Change Events, Change Orders
Procore for Government offers a structured workflow for managing changes that impact a public sector project's scope, budget, and schedule. The process tracks issues from a Potential Change Order through to an approved Change Order, which automatically updates both the prime contract (or funding) and the project budget, creating an audit trail.
Invoice Management
Key Tools: Prime Contracts / Funding, Commitments, Invoicing
Using the prime contract's (or funding's) SOV, users can generate payment applications to send as a bill to the project owner. Simultaneously, the solution can be configured to manage incoming invoices from subcontractors against their commitments, allowing users to approve and track payments and retainage.
Important
All financial activities, including the exchange and tracking of lien waivers and the processing of all payments, must be conducted using your organization's own approved financial and payment systems. Procore for Government manages the documentation and approval workflows that precede a transaction; the final processing of funds must occur outside of the platform.Project Management
PROCORE FOR GOVERNMENT
Available Procore for Government Tools are engineered consistent with the FedRAMP Moderate baseline.
Procore for Government’s Project Management tools unite every phase of your project on one secure platform, providing teams with access to critical documents, tasks, and reports.
Project Management Tools
Authorized users can access Procore for Government's Project Execution tools from the project navigation menu. Click the tools under Core Tools or Project Management in the menu.

Key Solutions
Procore for Government's project management tools provide a centralized hub for all project-related activities and documentation, allowing the entire team to work from the most current information.
Document Management
Key Tools: Documents, Forms, RFIs, Specifications, Submittals
Procore for Government's Drawing and Photo Management tools provides government agencies and their contractors with a centralized platform that offers automated version control, allowing teams to work from the most current images. Each revision is automatically archived, creating an auditable history. Access to drawings and photos provides authorized users with mobile and offline access in the field.
Drawing & Photo Management
Key Tool: Drawings, Photos
Procore for Government's Drawing and Photo Management tools provides government agencies and their contractors with a centralized platform that offers automated version control, allowing teams to work from the most current images. Each revision is automatically archived, creating an auditable history. Access to drawings and photos provides authorized users with mobile and offline access in the field.
Field & Task Management
Key Tools: Daily Log, Inspections, Observations, Photos, Tasks
Procore for Government's Tasks tool centralizes all project action items, allowing teams to create, assign, and track work in one place (instead of using scattered emails or spreadsheets). This assigns clear owners and due dates for every task, from simple reminders to critical path activities. The tool also streamlines communication and provides visibility into progress.
Assignment functions are also available. Users can document job site activity in the Daily Log and Photos tools and assign action items in the Tasks, Inspections, and Observations tools.
360 Reporting
Key Tools: 360 Reporting
Procore for Government's Project level 360 Reporting tool provides a real-time view of a project's health by consolidating data from across the platform into customizable dashboards and reports. Its key feature is the ability to offer a holistic, 360-degree perspective on project performance. Unlike traditional reports that are often outdated by the time they are compiled, 360 Reporting provides access to recent project data. Users can also create different report views for various stakeholders and control viewing using permission-based access.
Meeting Management
Key Tools: Meetings
Procore for Government's Meetings allows project teams to create and distribute agendas linked to project items. During the meeting, users can capture minutes in real-time, assigning specific action items to individuals with set due dates. Afterwards, the finalized minutes can be formally distributed, creating an official record and allowing stakeholders to track the status of assigned tasks directly within the platform.
Mobile Functionality
Key Tool: Procore Mobile App (iOS/Android)
The Procore mobile app provides a secure, unified platform that connects field operations directly to the office. It equips your teams with mission-critical tools, including Drawings, RFIs, and Daily Logs, on authorized government mobile devices. To help ensure the highest level of security for sensitive project information, access is strictly controlled through Procore for Government credentials and verified with Multi-Factor Authentication (MFA). For details, see Mobile Experience.
Quality & Safety
PROCORE FOR GOVERNMENT
Available Procore for Government Tools are engineered consistent with the FedRAMP Moderate baseline.
Procore for Government's Quality & Safety module connects real-time field observations, standardized inspections, and detailed incident reports, allowing users to identify trends and make data-driven decisions on project quality and worker safety that may impact projects.
Quality & Safety Tools
Authorized users can access Procore for Government's Quality & Safety tools from the project navigation menu. Additional tools are available at the company level.
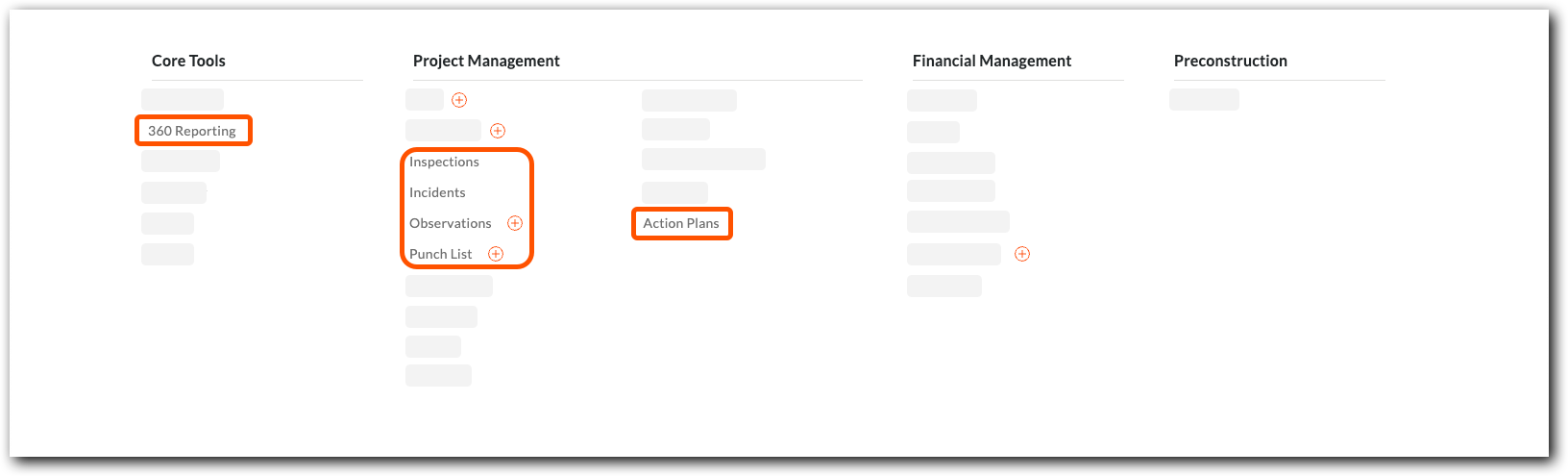
Key Solutions
Key solutions include:
Proactive Hazard Prevention
Key Tools: Action Plans, Forms, Observations
Procore for Government allows teams to standardize safety planning by digitizing Forms like Job Hazard Analyses and using mobile Observations to capture potential hazards. For systemic issues, multi-step Action Plans are deployed to manage and track corrective measures.
Standardized Inspections & Quality Control
Key Tools: Inspections, Punch List
Procore for Government's Inspections and Punch List tools provide structured workflows. Using mobile devices, teams conduct ongoing inspections with custom checklists, automatically assigning any deficiencies for correction. The Punch List tool then allows for tracking of all final contractual items from the field.
Incident Management & Reporting
Key Tool: Incidents, 360 Reporting
Procore for Government provides a comprehensive incident management and reporting system to document events and learn from the data. The Incidents tool provides a structured workflow to capture critical information following an event—from witness statements to root cause analysis—while automating compliance reports for your organization, such as OSHA logs. This data is also aggregated in 360 Reporting, which uses customizable dashboards to visualize incident trends across projects.
Getting Started Guides
PROCORE FOR GOVERNMENT
Available Procore for Government Tools are engineered consistent with the FedRAMP Moderate baseline.
Choose your guide below to get started.
Get Started for Administrators
Click here to view the steps.
Background
Procore for Government is FedRAMP® Moderate Authorized. Unlike the Procore commercial platform, this environment requires a more controlled onboarding process to help ensure all access is secure and auditable. Key principles of this environment include:
- Assisted Onboarding: Procore actively assists with the initial company and Single Sign-On (SSO) setup to help ensure proper configuration.
- Mandatory SSO: All internal employees are required to authenticate using your organization's SSO provider, eliminating the need for separate Procore for Government passwords.
- Invite-Only Access: All users, including subcontractors, must be explicitly invited to the Procore for Government platform by your organization's administrator. There are no free or public accounts.
Prerequisites
Before you begin, please ensure you have the following:
- Administrator Role: You have been authorized as the primary Administrator for your organization's Procore account.
- Procore Invitation: You have received an email invitation from Procore to activate your organization’s account.
- SSO Information: You have access to your organization's Identity Provider (IdP) metadata or configuration details needed for setting up SSO.
- User Lists: You have a list of official email addresses for the internal employees and external collaborators you plan to invite.
Steps
Follow these steps to configure your organization’s Procore account and onboard end users:
Step 1: Activate Your Administrator Account
Your first step is to activate your organization’s account, which must be created for you by Procore.
- Locate the invitation to Procore for Government in your email inbox.
- Click the link in the email to begin the setup process.
- You will be prompted to create a secure password for your administrator account.
- Follow the on-screen instructions to set up Multi-Factor Authentication (MFA). This is a mandatory security measure for all accounts that use a password in the Procore for Government environment.
Step 2: Configure Single Sign-On (SSO)
Next, you will work with Procore to connect your organization's Identity Provider (e.g., Okta, Azure AD, and so on) to your organization’s Procore account.
- Contact your designated Procore for Government Point of Contact to initiate the SSO setup.
- Provide your specialist with the required IdP metadata from your organization's IT department.
- An authorized member of the Procore for Government team must configure the connection on the backend.
- Once configured, work with your designated Procore for Government Point of Contact to test the SSO connection by logging out and logging back in through your organization's SSO portal.
Step 3: Invite Employees
After your SSO is active, you can begin inviting your team members. Team members will authenticate using the established SSO connection.
- Navigate to the company's Directory tool.
- Click Add People.
- In the Email Addresses field, enter the organization’s email addresses for all internal users you wish to invite.
- Assign a default Permission Template to define their initial access rights.
- Click Add. Your employees will receive an invitation email and will access Procore through your organization's SSO provider without needing to set a password.
Step 4: Invite External Collaborators (Subcontractors)
You can also invite users from outside your organization, such as subcontractors or consultants.
- Navigate to the company's Directory tool.
- Click Add People.
- Enter the email addresses of the external collaborators.
- Assign an appropriate Permission Template, which is typically more restrictive than your internal templates.
- Click Add.
- If the collaborator already has an account in the Procore for Government environment, they will receive a notification to access your organization.
- If they are new to the environment, they will be prompted to create a new account with a password and MFA.
Next Steps
Once you have successfully invited your initial set of users, you can begin setting up your workspace:
- Create a Project: Navigate to the Portfolio tool to create your first project.
- Populate Project Directory: Add the relevant users from the Company Directory into your new Project Directory.
- Configure Permissions: Fine-tune user permissions for specific tools within your Procore project.
Get Started for New Users
Click here to view the steps.
Background
Your organization is using the Procore for Government platform to manage projects in a secure environment. Access is by invitation only to ensure that project information remains protected.Your login method will depend on your user type:
- Internal employees will log in using their standard organization credentials via Single Sign-On (SSO).
- External collaborators (e.g., consultants, partners, subcontractors) will log in using an email address and a password secured with Multi-Factor Authentication (MFA).
Prerequisites
-
You must receive an email invitation from your organization's Procore Administrator to join the Procore for Government environment.
Steps
Please follow these steps to access your project.
Step 1: Locate Your Invitation and Begin
This first step is the same for all users.
- Check your inbox for an email with the subject line "Invitation to Procore".
- Open the email and click the link or button to accept the invitation.
Step 2: Choose Your Path to Log in to Procore for Government
After clicking the link in the invitation, follow these instructions for your specific role.
- Path A: For Internal Agency Employees:
Follow this path if you are an employee of the government agency that owns the Procore for Government account. Note: You will NOT need to create or manage a separate password for Procore for Government.- After clicking the invitation link, your web browser will automatically redirect you to your organization's familiar login page.
- Enter your standard work username and password (the same credentials you use to access your email or other company systems).
- Once you have successfully authenticated, you will be redirected to Procore for Government.
-
Path B: For External Collaborators:
Follow this path if you are a consultant, partner, or subcontractor invited to the Procore for Government project.- After clicking the invitation link, you will be directed to the Procore for Government login page.
- Your next step depends on whether you have joined the Procore for Government environment before.
- If this is your FIRST time, you will be prompted to create a new account:
- Enter your name and create a strong password for your account.
- Follow the on-screen prompts to set up Multi-Factor Authentication (MFA). This is a mandatory security step that requires you to verify your identity using a secondary method, such as an organization-approved authenticator app on your smartphone.
- If you already have MFA setup for Procore for Government:
- Simply enter the email address and password for your existing account.
- Complete the MFA prompt to sign in securely.
- If this is your FIRST time, you will be prompted to create a new account:
Step 3: Accept Mandatory Legal Notice
Before you can access your project, you must accept the terms of use for the platform.
- After successfully logging in for the first time, you will be presented with a Mandatory Legal Notice. This notice outlines the terms of use, data handling policies, and user responsibilities specific to the Procore for Government environment.
Important
You will not be able to access the Procore platform until you have accepted this notice. This is a one-time action required upon your first login. - Read the notice carefully. To proceed, you must click the Accept or Agree button at the bottom.
Next Steps
Congratulations on logging in! Here are a few things you can do now:
- Explore the Project: Once you are logged in, you are directed to the project's Home page.
- Update Your Profile: Click your initials or photo in the top-right corner to access your profile settings.
- Start Collaborating: Begin using the Procore tools you have been given access to, such as Drawings, RFIs, Submittals, and others.
Tutorials
This page is under construction.
Commercial Documentation
PROCORE FOR GOVERNMENT
Available Procore for Government Tools are engineered consistent with the FedRAMP Moderate baseline.
Welcome to the Documentation hub. For your convenience, the following links direct to documentation for the Procore commercial platform, as its user experience is similar to Procore for Government. While this commercial platform content helps end users understand general features and workflows, they are intended for informational purposes only.
The Procore for Government platform is distinct from the Procore commercial platform and has a unique set of features. The functionality, features, and services of Procore for Government are described in Product Deep Dive and Product Modules.
Important
By referencing the available documentation on this website (support.procore.com), all Procore for Government users acknowledge that all materials are based on Procore's commercial product and that it is the user's responsibility to account for any variations present in the Procore for Government platform.| Company Tools (Commercial Documentation) | Project Tools (Commercial Documentation) |
|---|---|
Release Notes
PROCORE FOR GOVERNMENT
Available Procore for Government Tools are engineered consistent with the FedRAMP Moderate baseline.
Below are notable updates about Procore for Government.
Recent Changes
Procore Achieves FedRAMP® Moderate Authorization (01/29/2026)
Procore for Government has achieved FedRAMP® Moderate Authorization. View the official listing on the FedRAMP Marketplace . Designed specifically for organizations that require government-grade security with a moderate impact rating, Procore for Government helps government agencies collaborate on public sector construction projects. To learn more, see Procore for Government.
FedRAMP® Moderate Equivalency Achieved (10/20/2025)
Procore is pleased to announce that Procore for Government has achieved FedRAMP® Moderate Equivalency through a 3PAO Assessment (Procore for Government is currently “In Process” on the FedRAMP Marketplace ). With this achievement, Procore can better support federal contractors on Department of Defense projects by helping them meet their security requirements for Cybersecurity Maturity Model Certification (CMMC) Level 2 compliance. To learn more, visit Procore for Government.
Shared Responsibility Model
Version 1.5
In the Procore for Government (PfG) environment, the responsibility for security operates under a clear Shared Responsibility Model that aligns with FedRAMP Moderate requirements. Procore, as the Cloud Services Provider (CSP), operates at the SaaS layer, inheriting security controls for the underlying infrastructure from AWS GovCloud.
The customer (agency or contractors) retains sole responsibility for managing everything above the platform layer. This includes authorizing user access, enforcing mandatory mobile device policies, configuring their Identity Provider (IdP) for Multi-Factor Authentication (MFA), and auditing user accounts against their own organizational compliance requirements. Both parties must actively collaborate and follow defined protocols to ensure the confidentiality, integrity, and availability of federal information.
To ensure you have the most comprehensive and up-to-date security information and guidance tailored to your specific system implementation, please contact your PfG Account team.
Access Control Family (AC)
| Customer Responsibility | Procore Responsibility | ||
|---|---|---|---|
| AC-2(a), AC-2(b), AC-2(c), AC-2(d), AC-2(e), AC-2(f), AC-2(g), AC-2(h), AC-2(i), AC-2(j), AC-2(k), AC-2(l) |
Account Management |
The customer is exclusively responsible for Company Account Management within PfG. Upon signing a contract, the customer must create an account using an email address and appoint an Administrator. Access to PfG is tightly controlled through customer-defined user groups, which are composed of fine-grained permissions (e.g., hiring manager, recruiter, administrator groups).
|
Create and manage system-level accounts (admin, service, maintenance); enforce least privilege and disable inactive accounts; integrate with IdP where applicable. |
| AC-2(1), AC-2(4), AC-2(5), AC-2(7)(a), AC-2(7)(b), AC-2(7)(c), AC-2(7)(d), AC-2(9), AC-2(12)(a), AC-2(13) |
Account Management |
The customer holds the sole responsibility for the lifecycle and security management of all PfG user accounts within their tenancy, adhering to their organization's policies.
|
Manage the underlying infrastructure, operating system, and security configurations required to support customer accounts, including system-level resource allocation and protection. This ensures the foundational platform is secure and available for the customer to perform all mandated user-level account administration and access enforcement. |
| AC-3 | Access Enforcement | The customer is responsible for establishing and maintaining the logical access policy, defining user roles and privileges (like ensuring least privilege and separation of duties), and actively assigning and managing those roles to the personnel. | Implement role-based access controls (RBAC) on Procore systems; enforce policy through IAM, console permissions, and MFA; verify access prior to granting privileges. |
| AC-5(a), AC-5(b) |
Separation of Duties | The customer is responsible for defining and documenting Separation of Duties (SoD) for individuals authorized to access the PfG application within their organization. Access control is implemented by the customer through custom roles designed to ensure SoD is enforced. | Assign distinct roles for system administration, security operations, and compliance; enforce through IAM group policies. |
| AC-6 | Least Privilege | It is the customer's responsibility to define PfG access authorizations to support the principle of least privilege within their organization. | Restrict Procore staff access to only the resources required for operational duties; regularly review elevated privileges; enforce just-in-time access for sensitive actions. |
| AC-8(a), AC-8(b) |
System Use Notification | When using identity federation and Single Sign-On (SSO) to log into PfG, the customer is responsible for ensuring that their Lightweight Directory Access Protocols (LDAP) and/or Active Directory (AD) systems display a compliant system use notification message or banner. Furthermore, the customer must ensure the notification message or banner meets FedRAMP requirements and remains on screen until users acknowledge the usage conditions and take explicit action to log on or further access the system. | Display login banners on Procore systems notifying of authorized use only, per FedRAMP and agency guidance. |
| AC-19(a), AC-19(b), AC-19(5) |
Access Control for Mobile Devices | For the Procore for Government Mobile App, the customer bears responsibility for enforcing all mobile device policies (including those applicable to their subcontractors) to ensure responsible use. | |
| CA-6(a), CA-6(b), CA-6(c), CA-6(d), CA-6(e) |
Authorization |
The federal customer, or agency, operating within the Procore for Government environment holds the final responsibility for Authorizing System Operation.
|
Obtain and Maintain FedRAMP ATO. Ensure the SSP, SAP, SAR, and POA&M remain current; notify the PMO and AO of significant changes or incidents. |
Identification and Authentication Family (IA)
| Column | Type | Customer Responsibility | Procore Responsibility |
|---|---|---|---|
| IA-8, IA-8(1), IA-8(2)(a), IA-8(2)(b), IA-8(4) |
Identification and Authentication (Non-Organizational Users) |
The customer is responsible for integrating the Procore for Government accounts with their agency's Single Sign-On (SSO) capability using their Identity Provider's (IdP) identity federation. For agency customers mandated to use a hardware-based smartcard, the system supports integrating this card (such as a PIV card or CAC) with SSO through SAML identity federation. The customer holds the responsibility for successfully completing the integration of the PIV card or CAC with the Procore for Government environment |
|
| IA-11 | Re-authentication | Customers are responsible for configuring their Identity Provider (IdP) to ensure users are re-authenticated following periods of inactivity and to strictly enforce mandatory session timeouts as required by security policy. |
Incident Reporting Family (IR)
| Column | Type | Customer Responsibility | Procore Responsibility |
|---|---|---|---|
| IR-6(a), IR-6(b) |
Incident Reporting | The customer is responsible for reporting all suspected security incidents or system events to Procore via email at security@procore.com. Additionally, Federal government customers must adhere to their separate reporting obligations, which include reporting incidents to CISA as required by OMB Memo M-07-16. |
Report incidents to FedRAMP PMO, AO, and impacted customers within 1 hour or confirmation per FedRAMP guidance. Submit follow-up reports (24 hr, 3 day, 30 day). DoD reporting within 72 hours. |
| IR-9(b) | Information Spillage | Customers are responsible for identifying the specific information involved in the information system contamination and for notifying Procore of potential information spillage within their tenant environment via established communication methods within the cloud service agreements. | Maintain documented spillage response procedures (e.g., handling CUI/PII); immediatly isolate and sanitize affected systems. |
Risk Assessment Family (RA)
| Column | Type | Customer Responsibility | Procore Responsibility |
|---|---|---|---|
| RA-2(c) | Security Categorization | Each government customer utilizing the PfG system is responsible for designating an AO. The AO must review the SSP, which includes the determined security categorization, as part of the FedRAMP package for the PfG system and authorize the system for their organization's use. |
System & Services Acquisition Family (SA)
| Column | Type | Customer Responsibility | Procore Responsibility |
|---|---|---|---|
| SA-4(10) | Acquisition Process | Customers can integrate PfG with their SSO through SAML 2.0. Customers are responsible for using only PIV or CAC credentials that are on the FIPS 201-approved product list. |
Contact Support
PROCORE FOR GOVERNMENT
Available Procore for Government Tools are engineered consistent with the FedRAMP Moderate baseline.
Contact Support
Support for Procore for Government is available in English. Live chat is not available.
|
|
Hours of Operation:
|
When contacting support: |
