Configure SP-Initiated SSO for Procore in Azure AD (Entra ID)
Note
If your organization is using the Portfolio Financials and Capital Planning products in Procore, you will need to reach out to your Procore point of contact or the Support team to set up your Azure AD SSO.
You will need to provide the following information when requesting the setup: Single Sign On Issuer URL, Single Sign On Target URL (Optional for IdP-Initiated SSO), and Single Sign On x509 Certificate.
Objective
To configure SP-initiated Single Sign-On (SSO) for Procore in Microsoft Azure Active Directory (Azure AD).
Background
If your company wants to use Azure AD SSO to manage user logins to Procore, these configurations are supported:
- Service Provider Initiated (SP-initiated) SSO. Referred to as Procore-initiated SSO, this option gives your end users the ability to sign into the Procore Login page and then sends an authorization request to the IdP. Once the IdP authenticates the user's identify, the user is logged into Procore. To configure this solution with Microsoft Azure AD, see the Steps below.
OR - Identity Provider Initiated (IdP-initiated) SSO. With this option, your end users must log into your Identity Provider's SSO page (for example, Azure AD) and then click an icon to log into and open the Procore web application. To configure this solution, see Configure IdP-Initiated SSO for Microsoft Azure AD.
Things to Consider
- Required Permissions:
- Global Administrator rights to Azure AD.
AND - 'Admin' level permissions to Procore's Company level Admin tool.
- Global Administrator rights to Azure AD.
- Prerequisites:
- Complete all the Preparation Phase steps outlined in Setup Guide: Microsoft Azure AD.
- Supported Azure AD Editions:
- Microsoft Azure Active Directory
- Supported Authentication Protocol:
- Security Assertion Markup Language (SAML 2.0)
- Additional Information:
Steps
- Step 1: Add Procore as a New Enterprise Application in Azure AD
- Step 2: Configure the Procore Enterprise Application's SSO Settings
- Step 3: Add the Azure AD Settings to Procore's Company Level Admin Tool
Step 1: Add Procore as a New Enterprise Application in Azure AD
- Log in to the Azure AD portal as a Global Administrator: http://portal.azure.com
- Under Favorites, click Azure Active Directory.
- Under Manage, click Enterprise Applications.
- Click +New Application.
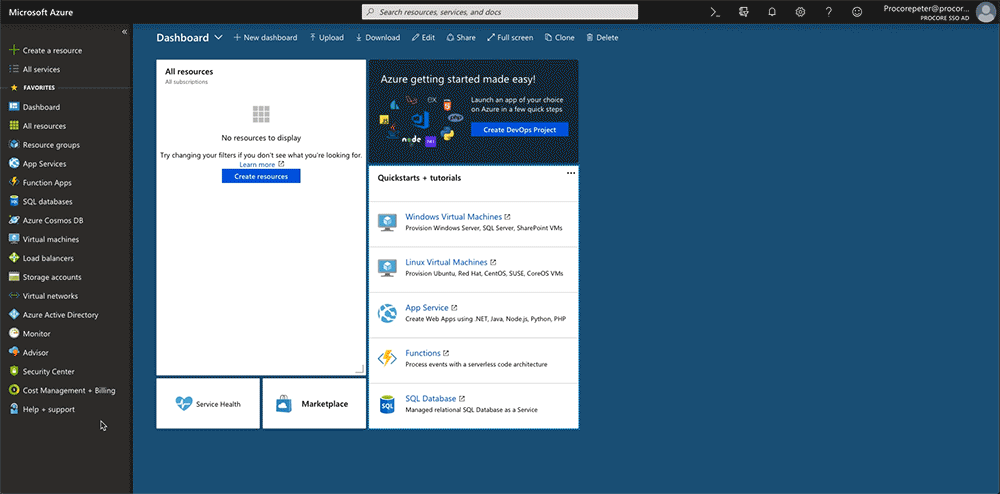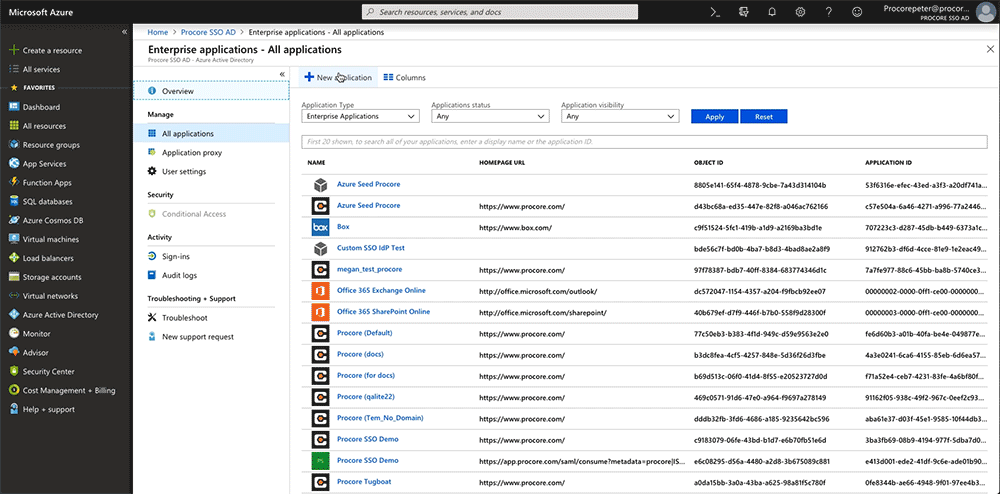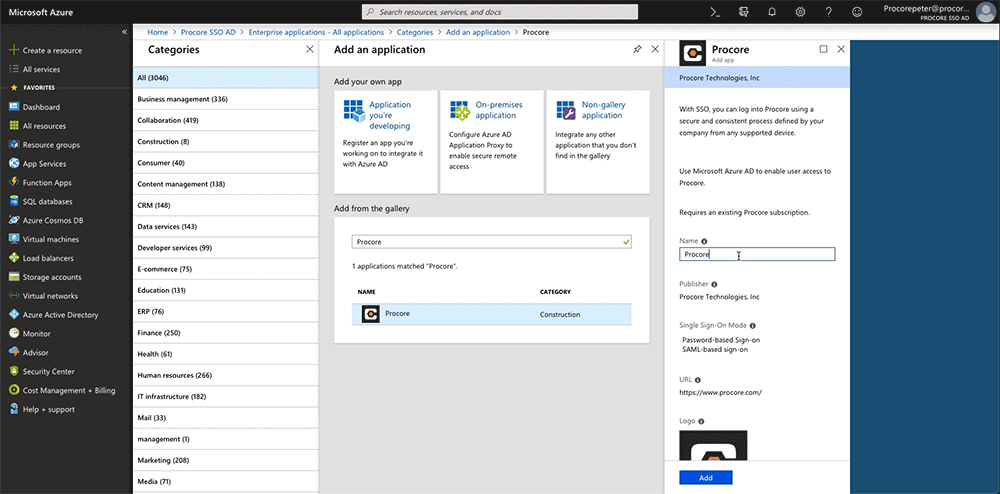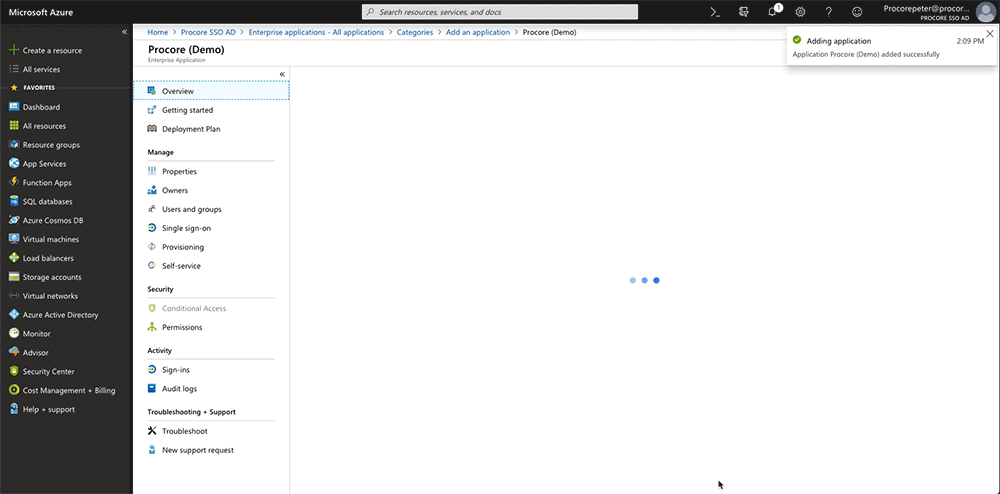
- Under Add from the Gallery, type the following in the Enter a Name box: Procore
- Click the matching application named Procore.
This reveals a new pane. - In the Name box, type a name for your application.
Note: In the example above, we named our application: Procore (Demo) - Click Add.
A message appears to confirm that the application was added successfully. You should now be viewing your new Procore enterprise application's Overview page.
Step 2: Configure the Procore Enterprise Application's SSO Settings
- In the Overview page for your new enterprise application, under Manage, click Single Sign-On.
- In the Single Sign-on Mode page, click SAML.
This opens the Set Up Single Sign-On with SAML - Preview page. - Under Basic SAML Configuration, click Edit.
This opens the Basic SAML Configuration window. - Under the Basic SAML Configuration page, do the following:
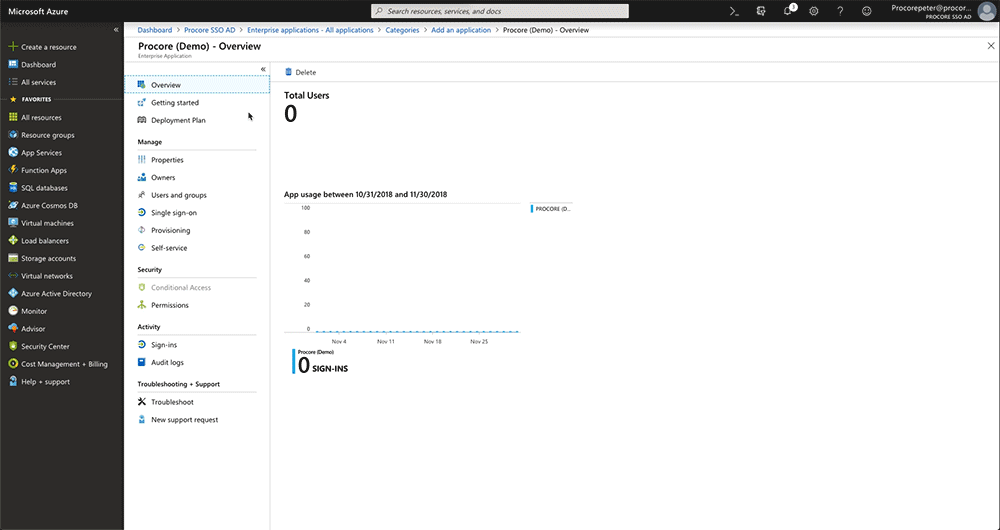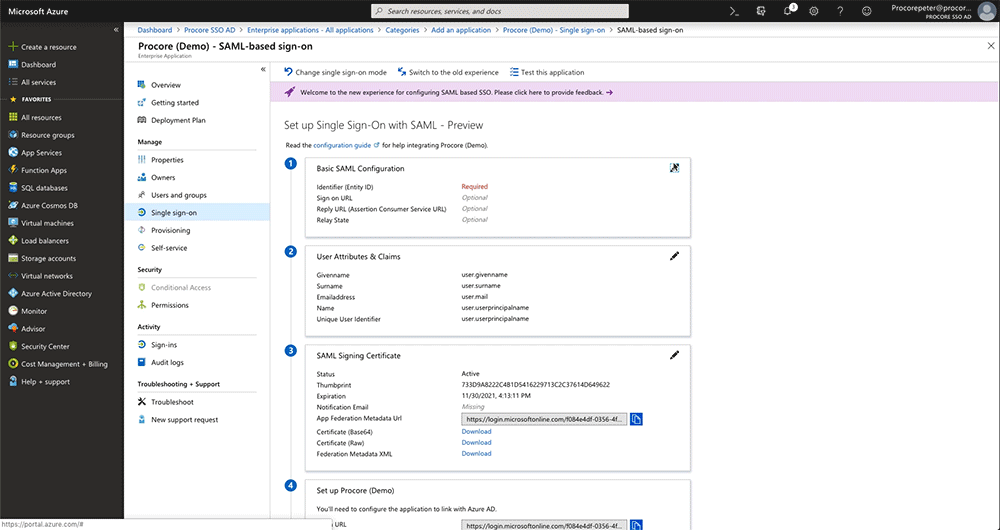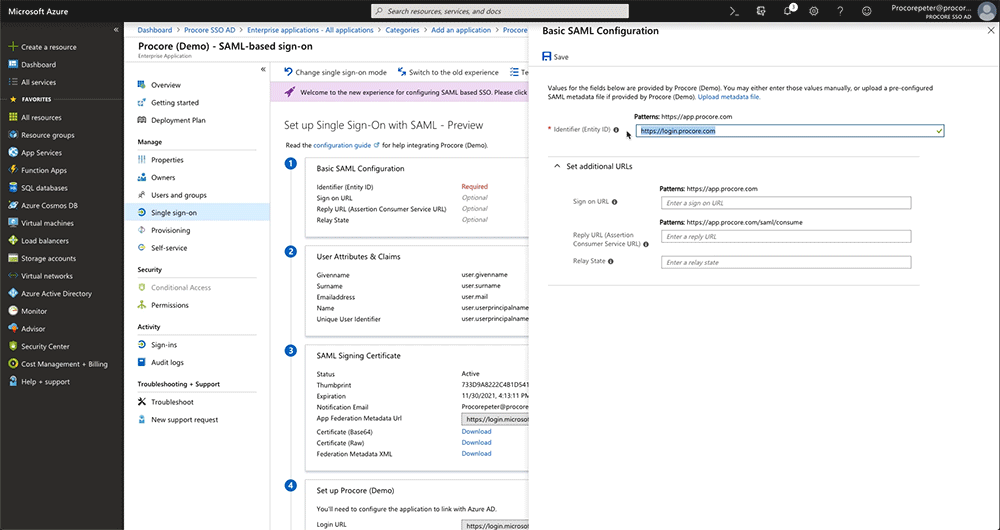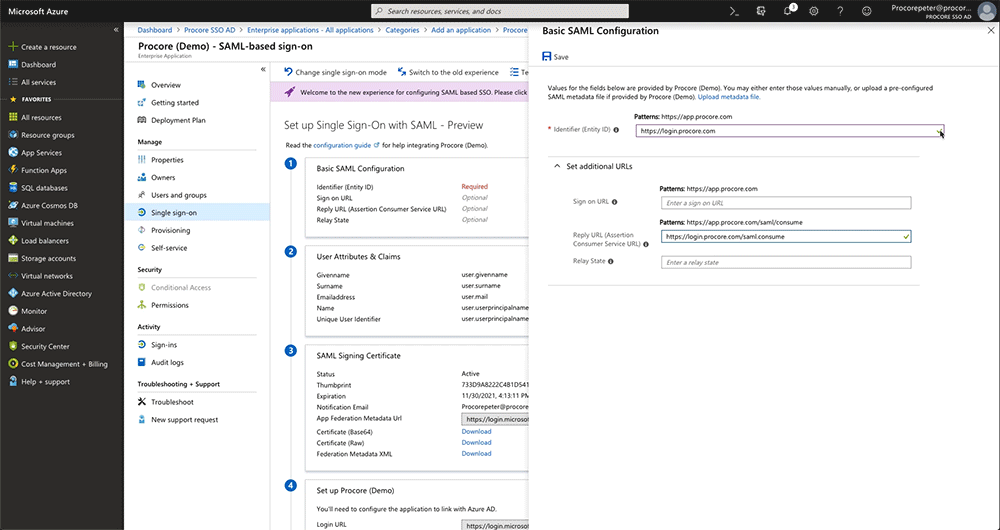
- Identifier (Entity ID)
Change the value from:https://app.procore.comto:https://login.procore.com
Note: If you are using Portfolio Financials and Capital Planning, enter the following value instead:https://www.honestbuildings.com/pfcp/app/#!/login
- Sign On URL
Leave this field blank. You do NOT need to enter a value in this field. - Reply URL (Assertion Consumer Service URL)
Enter the following:https://login.procore.com/saml/consume
- Identifier (Entity ID)
- Click Save.
A message appears to confirm that your settings were saved successfully. - Click the 'x' to close the Basic SAML Configuration page.
- Under SAML Signing Certificate, click the Download link for the Certificate (Base64) file.
Notes:- This downloads a file named PublicCertificate.cer to your browser's specified download area.
- Open the file in a text editor and leave it open on your computer. Later, you will copy the code that appears between the ---BEGIN CERTIFICATE--- and ---END CERTIFICATE-- tags into Procore.

Step 3: Add the Azure AD Settings to Procore's Company Level Admin Tool
- Leave the Azure AD page open as described in the previous step.
- Log into Procore using your Procore Administrator account.
- Navigate to the Company level Admin tool.
- Under Company Settings, click Single Sign On Configuration.
- Leave Procore's 'Single Sign On Configuration' page open.
- Go to the Azure AD page that you left open.
- Under Set Up [Your Application Name], click View Step-by-Step Instructions.
This opens the Configure Sign-On page.
Copy this information from Azure AD… Paste it into this field in Procore… SAML Entity ID
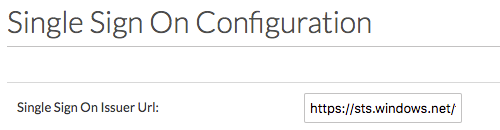
Copy the URL in this field from Azure AD.Single Sign On Issuer URL
Paste the SAML Entity ID URL into the Single Sign On Issuer URL field.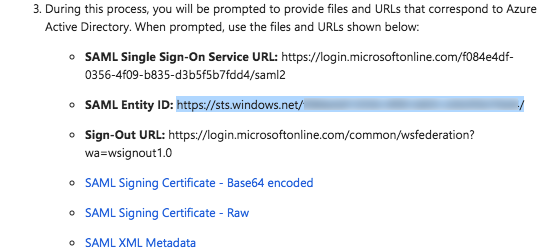
SAML Single Sign-On Service URL
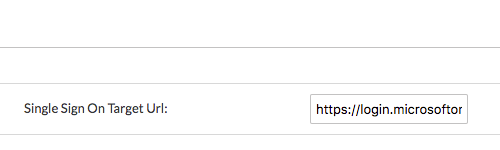
Copy the URL in this field from Azure AD.Single Sign On Target URL
Paste the SAML Single Sign-On Service URL into the Single Sign On Target URL field.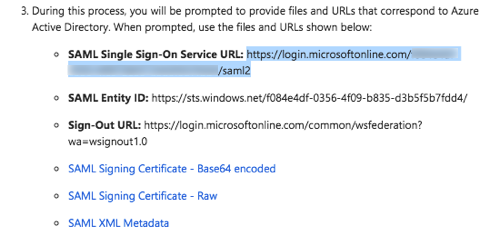
SAML XML Metadata
Download this file to your computer and open it in a text editor (i.e., Notepad or Text/Edit). Locate the certificate data that appears between the HTML start and end tags for the x509 certificate. Then copy the data. Do NOT copy the tags. This is depicted in the animated image above:Start Tag: <X509Data><X509Certificate>
End Tag: </X509Data></X509Certificate>
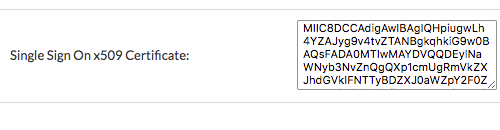
Single Sign On x509 Certificate
Paste the certificate data you copied into this field.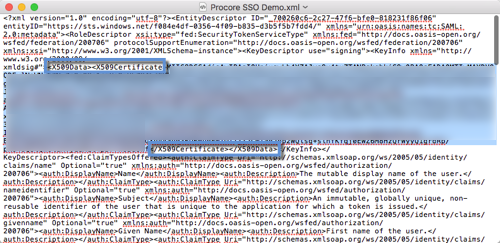
- On the 'Single Sign On Configuration' page in Procore, click Save Changes.
- Reach out to Procore Support or your company's Procore point of contact to request they configure the email domain(s) you'd like to target for SSO.
- After you receive confirmation that the SSO configuration is ready, mark the Enable Single Sign On checkbox on the 'Single Sign On Configuration' page.
- Select the Service Provider Forward option.
- Click Save Changes.
PROCORE SUPPORT: INTERNAL NOTE
Perform the steps below when notified by the Procore Administrator that the SSO configuration is complete:
- When notified by the Procore Administrator that the SSO configuration is complete, please be sure that the following fields are filled out:
- Single Sign On Issuer URL
- Single Sign On Target URL
- Single Sign On x509 Certificate
- Once the above is confirmed, make a request on behalf of the client in one of the following Slack channels to have the desired email domain(s) targeted for login with SSO:
- #cs-sso-questions
- #dept-cs-core
- Once email domain(s) have been entered into the configuration by our internal team, the client will be able to check the box for 'Enable Single Sign On'. When they do, they will see the following options: ' Allow Password Login' (refers to IdP-Initiated) and 'Service Provider Forward' (refers to SP-initiated). We typically recommend they try 'Allow Password Login' first for testing purposes (this will allow the admin to log back in and disable SSO for troubleshooting if the SSO configuration results in an error).


