Procore Initiated SSO - Reuse
Reuse
Superuser Only
Add the Single Sign On Domain(s) to Procore
Important
Before adding the SSO settings from the supported integration into Procore, ensure that you have done the following in the SSO provider's console (e.g., Azure AD, Okta, or OneLogin). After those changes have been made, make sure that you update the x509 certificate with the SSO provider before copying them into Procore using the steps below.
Change from: https://app.procore.com
Change to: https://login.procore.com
Change from: https://app.procore.com/saml/consume
Change to: https://login.procore.com/saml/consume
- Log into Procore as a Superuser.
- Determine if the client requires one of the following
- Single Domain SSO Support
With single domain support, the client's end users will log into Procore from a single domain. Typically, this is the same domain as the end users email address. However, this is NOT always the case with all customers. You must verify the domain name entry with the customer's Procore Administrator.
OR - Multiple Domain SSO Support
With multiple domain support, the client's end users will log into Procore from multiple domains. This is more common for enterprise customers, who may manage their end users across multiple domains. For example, if one Procore user's login email address is @example-east.com and another user's login email address in @example-west.com, you will need to enter BOTH those domains.
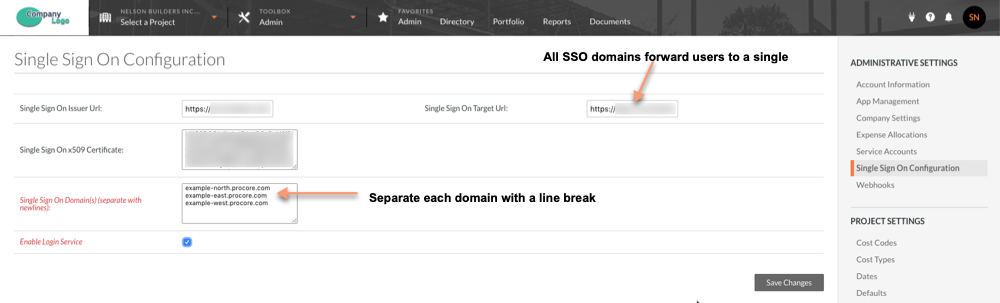
Important! There is no limit to the number of domains that you can enter in this list. However, you must separate each domain by a line break.
- Single Domain SSO Support
- Navigate to the Company level Admin tool.
- Under Administrative Settings, click Single Sign On Configuration.
- Ensure that the customer's Procore Administrator has entered the following information:
- Single Sign On Issuer URL. The issuer URL identifies the SAML provider. It is a unique URL that is provided to the client by the SSO provider (e.g., Azure AD, Okta, or OneLogin).
- Single Sign On Target URL. The target URL. There is always only one (1) URL, regardless of whether the client's account will use multiple domain support or single domain support.
- Single Sign On x509 Certificate. The certificate is always provided by the provider and entered by the client.
- In the Single Sign on Domain field, you can enter as many domains as needed. Make sure to separate each domain by a line break.
Note: All of the Single Sign On Domain entries will will forward to the Single Sign On Target URL.